News out of the Australian government this month provided a glaring reminder that the weakest link in the cybersecurity chain isn’t software vulnerabilities or patching cycles, it’s the person behind the keyboard.
Western Australia’s Office of the Auditor General (OAG) submitted its yearly Information Systems Audit Report to the Australian Parliament on Aug. 21, rendering damning conclusions for several agencies in Western Australia’s state government.
The highlight of the report, spreading like tech wildfire through the bush, was that government employees failed the basics of Password 101, or 123 in this case.
Sampling network accounts at 17 Australian government agencies, OAG found that 1,464 accounts had a password of “Password123.” The report lists the top 20 common passwords, all with at least 96 instances of use across agencies.
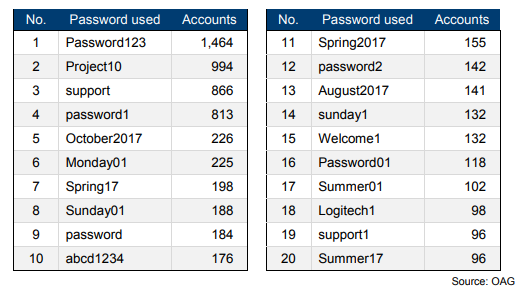
“We gained access to the agency’s network with full system administrator privileges by using an easily guessed password, Summer123,” OAG added, gaining access through a publicly-available resource.
One Aussie agency had 250 privileged accounts with poor password strength. You would think at this point that government employees–amid a high-profile breach of their personal information in 2017–would have learned their lesson and done their due diligence.
But in the U.S. Federal government, doubtless this problem is similar, owing to perhaps nothing more than human nature.
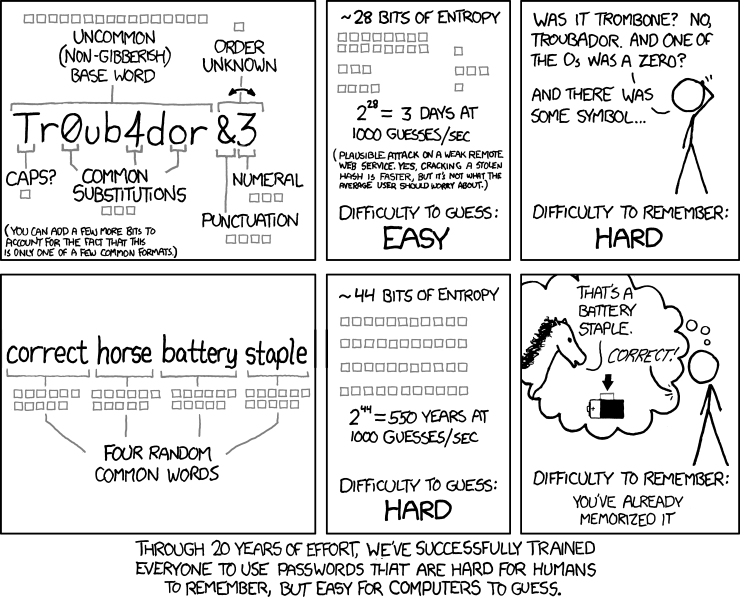
No one can knock the convenience, familiarity, and muscle memory associated with a simple password. Conscientious users do know to at least spice them up a bit. But the wisdom of adding “security” conventions–upper and lower-case alternation, 3’s for E’s, an extra wh@cky symbol–goes out the window when you end up with a daily task that’s more arduous than typing that default WiFi password on the back of your router–another security risk, but you didn’t bother updating.
Rinse and repeat multiple times each day, and you can understand why people don’t have the time or the patience. And even for the more judicious of the bunch, it seems we may have been teaching the wrong things. It turns out those “security” conventions hardly stack up.
It’s not a new Federal government problem. Going back nearly every year for the past 15–since the Department of Homeland Security’s establishment and passing of the Federal Information Security Management Act of 2002–DHS’ Office of Inspector General has flagged lack of password complexity and default passwords in DHS databases as glaring issues in its yearly Information Security Program audits.
As recently as December 2017, the National Institute of Standards and Technology updated and finalized its robust guidance on identity management and authentication, and NIST has additional publications for sector and industry-specific authentication.
Bloomberg Government wrote this month that DHS’ National Protection and Programs Directorate’s “most important role is safeguarding Federal agencies’ .gov domains from attack,” and said they are ramping up steps to do so. It could mean that NPPD mandates better password strength across agencies and holds agency heads accountable for failure to do so, Bloomberg suggested.
This month IBM released a white paper that found that “smart city sensor and control devices currently deployed across the globe by various municipalities” had recurring instances of public default passwords–opening entire local infrastructure to compromise. As we aim to connect our infrastructure and make them smart, the steps along the way seem exactly the opposite.
And not unlike phishing and social engineering exploits, it’s the little things that often do the most damage, with pilot error to guide them. The machine is never the problem. But we can use those machines to remedy our apparent lack of discretion.
Federal CIO Suzette Kent said this month that the government has “moved the needle with multi-factor identification to near 90 percent across 90 agencies.” Multiple factors mean that your weak password is just one step in the process of authentication.
The Federal CIO Council, according to Kent, has also undertaken a new zero-trust network pilot. Once you get past those multiple factors, you still don’t get free access to sensitive data.
Identity, Credentialing, and Access Management is top of mind for Federal agencies and the administration, and with good reason. But these efforts can only stem the tide of a persistent and very primitive problem.
Multifactor Authentication is inherently necessary, but a password will likely remain one of those factors–perhaps until we see a real biometric boom–so individual users may have to focus on the things they can control. Secure sites to check the strength of your password–and how long it would take a computer to crack it–are all over, and are pretty neat tools to play with. Western Australia was made an example, but no government is immune. It may be useful to think of that, and who else might know our pet’s name too, the next time any of us visit a login screen.

